Trisk Permission-Based Governance puts you in control. Define who sees, edits, or approves
critical information—across teams, clients, and external partners. Every document, task,
and approval is safeguarded with enterprise-grade security while remaining effortlessly accessible to
those who need it.
No accidental oversharing. No security gaps. Benefit from intelligent control over every piece of
business-critical information.
Implementing role-based access control (RBAC) has led to a 75% drop in security incidents by ensuring only authorized personnel access sensitive data. (BigID)
Permission-Based Governance provides administrative and productivity benefits, leading to an annual operating benefit of $43.71 per employee. (NIST)
Strict access controls help prevent nearly half of data breaches caused by credential misuse, protecting sensitive information. (Deloitte)
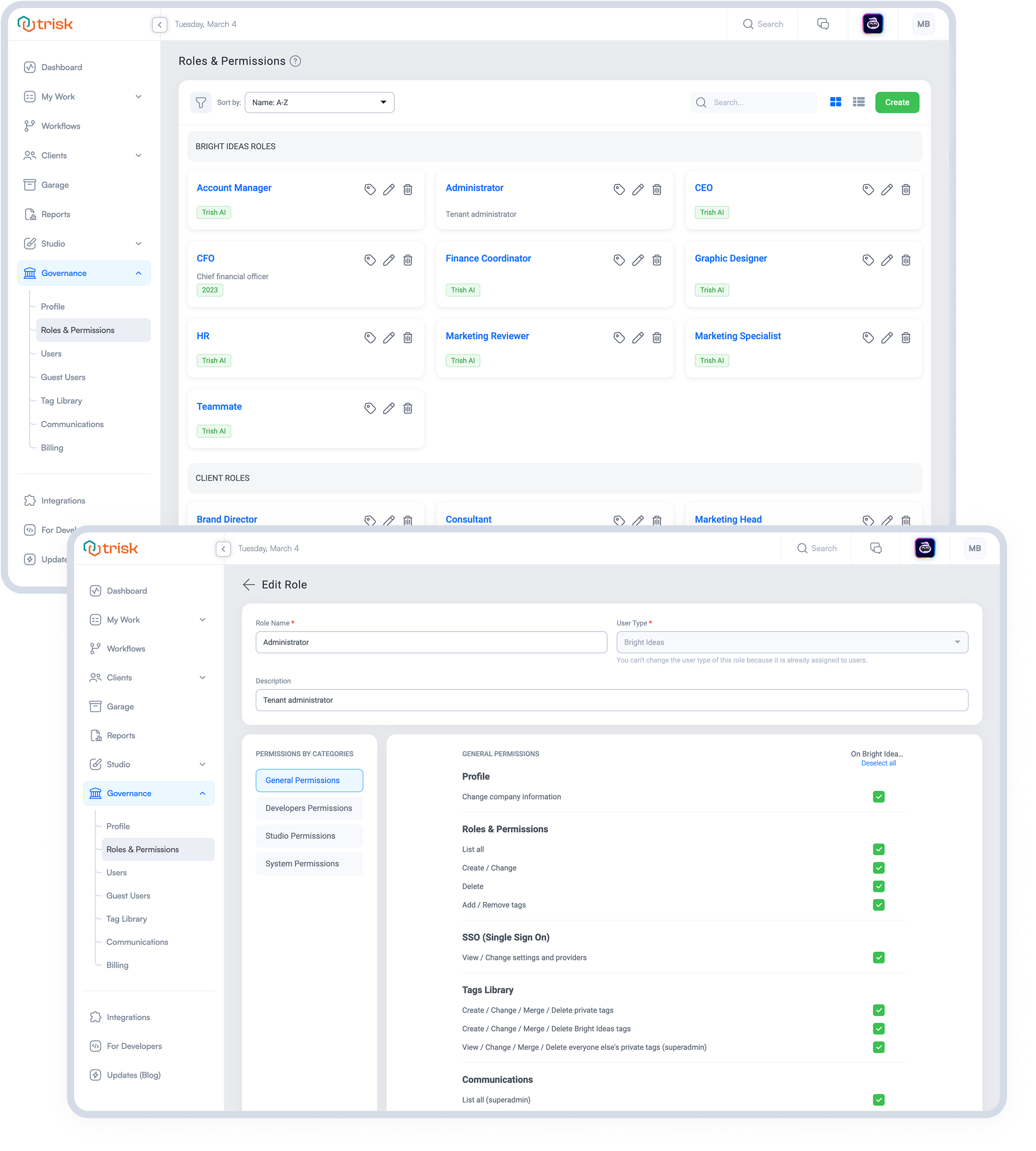
Sensitive business data demands precision control. Trisk’s Permission-Based Governance ensures the right people access the right information at the right time, safeguarding data integrity and operational security without slowing down workflows.
Built for professional services, Trisk replaces outdated, one-size-fits-all access models with granular, role-based permissions that empower efficiency while minimizing risk.
Trisk ensures data isn’t just protected—it’s intelligently managed, giving businesses full control, flexibility, and security without friction.
Use Permission-Based Governance for:
Your data security is our top priority. Trisk follows industry-leading standards to protect sensitive
information and ensure regulatory compliance.

Strict organizational controls to safeguard your data, the privacy of your clients and maintain confidentiality.

Secure payment processing ensures cardholder data protection with Stripe’s PCI DSS compliance.

Designed to protect the privacy and security of patient health information in healthcare-related workflows.

Regulates responsible handling of personal data for EU-based clients.

Financial industry standards to support compliance in regulatory environments.
Learn how businesses like yours leverage Trisk to streamline workflows, enhance collaboration, and achieve their goals. Discover real-world success stories and innovative ways Trisk transforms operations for maximum efficiency.
Optimize data collection and processing with dynamic, Excel-compatible forms supporting over 450 formulas. Enhance accuracy and speed in financial reporting, budgeting, and compliance tasks.
Store all your business-critical files securely with unlimited storage space, ensuring easy access and reliable backups.
Deliver an exceptional customer experience through personalized, self-service portals that provide 24/7 access to project updates, documents, and progress reports. Strengthen client relationships with transparency and real-time insights.
Streamline approvals and accelerate business transactions with unlimited e-signature requests. Securely sign, send, and manage contracts without limitations, ensuring fast, legally binding execution at no extra cost.
Available: Details Soon
Permission-based governance is a security framework that allows organizations to control who can access, edit, or approve specific data, documents, and workflows based on assigned roles and permissions.
Explore our flexible plans with per-active user model, all-in-one features, AI
assistance, and 30-day free trial with no credit card required